Zero-Knowledge encryption
Tiri Vault is built on a zero-knowledge encryption model, ensuring that no third party, including a
storage network, Tiri Vault itself, or any intermediary, can access user data. Tiri Vault encrypts all
files and metadata client-side before they ever leave a user’s device.
At the core of this encryption process is ChaCha20-Poly1305, a high-performance, authenticated
encryption scheme that provides both fast encryption and robust integrity verification. Any data that
leaves a client’s device, as well as corresponding metadata, including file names, folder structures,
and Content Identifiers (CIDs), is encrypted with a unique ChaCha20-Poly1305 key before being stored on
the blockchain.
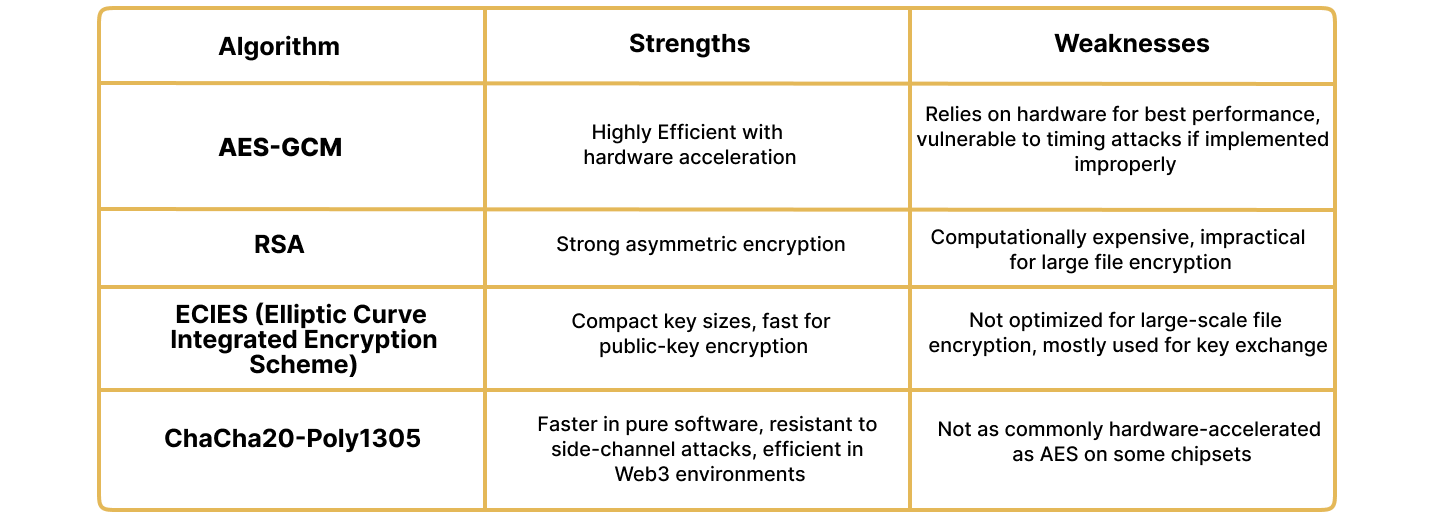
Encryption plays a critical role in decentralized storage, but not all encryption schemes offer the same
balance of security, efficiency, and usability. AES (Advanced Encryption Standard), RSA, or hybrid
models are widely used, but they present challenges that ChaCha20-Poly1305 overcomes.
While AES-GCM is common in Web2 cloud storage due to hardware acceleration, its performance drops
significantly on platforms without dedicated AES instructions. ChaCha20-Poly1305, in contrast, operates
with pure software efficiency, making it ideal for Web3 environments, including mobile, embedded, and
decentralized platforms where hardware acceleration may not be available.
Unlike RSA and ECIES, which are primarily used for key exchanges rather than full file encryption,
ChaCha20-Poly1305 enables scalable, high-speed encryption while ensuring message integrity with Poly1305
authentication.
ChaCha20-Poly1305's streaming capabilities enable on-the-fly encryption of files as they are being
uploaded or modified, making it possible for Tiri Vault to support real-time file synchronization. This
method makes Tiri Vault extremely scalable and practical for personal storage and collaboratio.
By implementing ChaCha20-Poly1305 encryption on the client-side, Tiri Vault ensures that:
-
User data remains completely private—no third party, including Tiri Vault, has access to files or
metadata.
-
Encryption performance is optimized for Web3, avoiding the reliance on hardware-accelerated AES.
-
Metadata privacy is preserved.
-
Streaming encryption allows real-time file synchronization, a key feature provided by Tiri Vault.
Tiri Vault's zero-knowledge encryption approach is designed for scalability, privacy, and efficiency,
making it a next-generation solution for truly private decentralized storage.
Tiri Relay
Currently, no pure Web3 storage networks provide instant file synchronization similar to Web2 workspace
services. Decentralized storage solutions prioritize security, redundancy, and immutability but lack the
real-time access needed for collaborative workspaces. The primary challenges include delayed file
retrieval, lack of in-place file modifications, and the need for frequent blockchain transactions to
reflect updates.
Tiri Relay is a solution to integrate a hybrid architecture that combines decentralized blockchain-based
storage with off-chain real-time synchronization mechanisms.
How Tiri Relay helps real-time file access in decentralized networks?
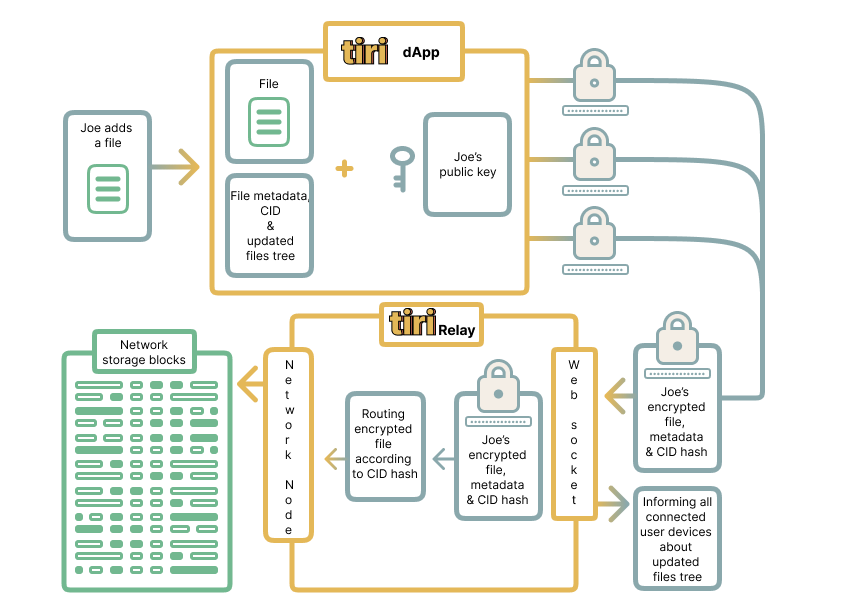
Zero-Knowledge Change Tracking: Tiri Relay maintains a user’s hierarchical file/folder
tree structure, ensuring efficient navigation and organization of stored data. This tree structure is
fully encrypted on the front-end side with a user’s public key, meaning that even Tiri Relay can not see
filenames, paths, file structures, or contents. Changes to files or folders modify the Merkle tree hash,
which serves as a cryptographic fingerprint of the entire file system. Zero-knowledge proofs allow user
devices to verify that a change has occurred (e.g., a file was updated, renamed, or moved) without
revealing the actual modifications and enable synchronization while maintaining full privacy.
WebSockets for Instant Synchronization: Tiri Vault employs an off-chain caching layer
on a local user device that allows instant updates to files and uses Tiri Relay to commit the latest
file versions to the decentralized storage network. Tiri Relay utilizes WebSockets to ensure real-time
synchronization across multiple devices. Users see changes reflected instantly.
Hash Commitments for Integrity Checks: To maintain trust and verify file authenticity
without storing every update on-chain, Tiri Vault uses hash commitments. This means that while the files
remain mutable in the short term, their integrity is cryptographically verified before finalizing on
decentralized storage.
Below is an overview of how a file is processed when added to a Tiri-synced local folder:
1. Detecting File Changes & Updating the FileTreeModel
When a user adds a new file to their Tiri-synced local folder, the Tiri Vault LocalFilesWatcher detects
the change and updates the FileTreeModel, a structured representation of the user's files and
folders.
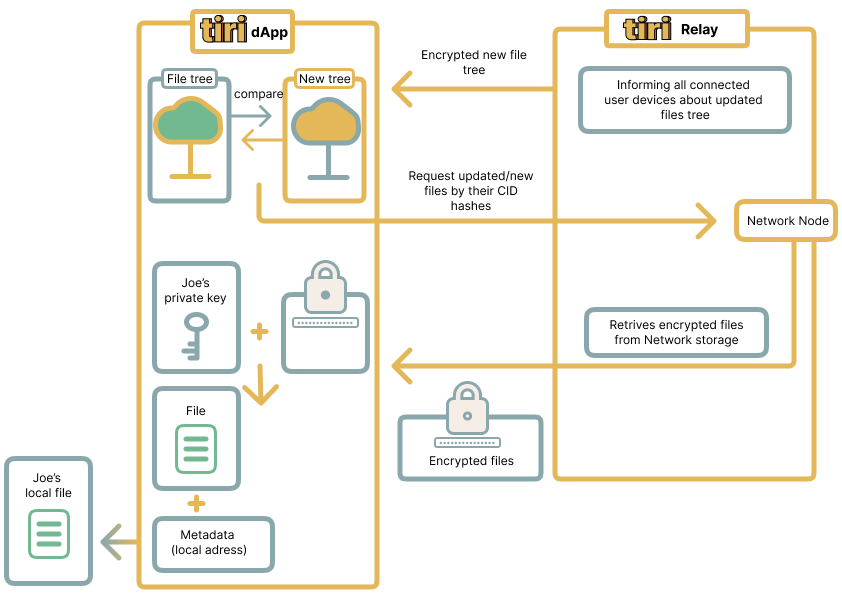
2. Requesting the Last Saved FileTreeModel Hash from Tiri Relay
The Tiri App queries the Tiri Relay for the latest saved FileTreeModel hash to check for any changes. If
this is the first synchronization, there is no stored FileTreeModel, so the newly generated model is set
as the actual one. If a hash exists, the Tiri App compares the retrieved hash with the hash of the new
FileTreeModel.
3. Resolving Differences Between Local and Stored File Trees
If the hashes don’t match, this means changes have occurred. The Tiri App then downloads the last stored
FileTreeModel from Tiri Relay, decrypts it using the user’s private key, compares it to the new
FileTreeModel and identifies four key differences (diffs):
Upload → Files that need to be uploaded to storage.
Remove → Files that need to be deleted from storage.
Download → Files that need to be downloaded to the local device.
LocalRemove → Files that need to be deleted from the local device.
Then it merges the changes and writes a new, updated FileTreeModel.
4. Processing File Synchronization
To ensure consistency and avoid conflicts, the Tiri App applies changes in a strict sequence: Remove →
Upload → LocalRemove → Download.
5. Updating FileTreeModel on Tiri Relay
Once all file operations are successfully completed, the merged FileTreeModel is encrypted with the
user’s public keyand uploaded to the Tiri Relay, replacing the previous version.
6. Notifying All Devices for Synchronization
Tiri Relay operates a WebSocket server that actively notifies all connected user devices whenever a new
FileTreeModel hash is saved.
When a device receives this notification, it requests the updated FileTreeModel, decrypts it, and
applies the necessary changes. This ensures that all user devices remain in sync, providing a seamless
and decentralized file collaboration experience.
When a file update occurs on another device, Tiri Relay ensures that all connected devices receive and
apply changes efficiently while maintaining end-to-end encryption and zero-knowledge privacy. Below is a
files update workflow:
1. Requesting the New FileTreeModel
The user’s device receives an update notification from Tiri Relay’s WebSocket server and requests the
latest FileTreeModel from Tiri Relay.
2. Resolving Differences
The Tiri App decrypts the new FileTreeModel using the user’s private key and compares the decrypted
FileTreeModel with the previously saved local version. The Tiri App identifies and processes four key
differences in the same strict sequence: Remove (files that need to be deleted from storage) → Upload
(files that need to be uploaded to storage) → LocalRemove (files that need to be deleted from the local
device) → Download (files that need to be downloaded to the local device).
3. Downloading Updated Files
New files required for synchronization are downloaded using their CID hashes through Tiri Relay. The
files are then decrypted on the device using the user’s private key. Once decrypted, the files are saved
locally according to their decrypted CIDs, preserving their original file structure.
4. Saving the Updated FileTreeModel as the Actual Version
If all updates are processed successfully, the new FileTreeModel is saved locally as the current actual
version.
This seamless synchronization workflow provided by Tiri Relay ensures that Tiri Vault users can work
across multiple devices without data loss, conflicts, or security compromises.
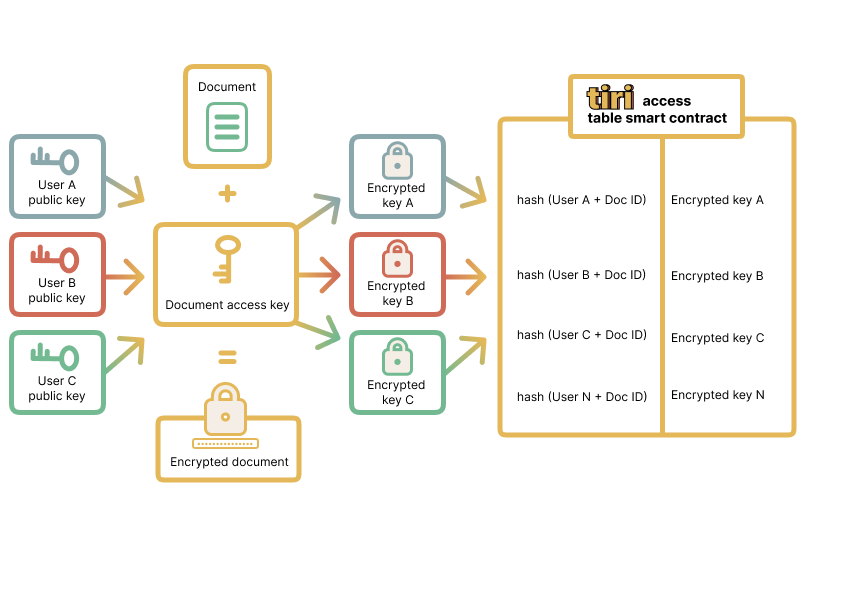
Asymmetric Key Wrapping
Tiri Vault implements a decentralized, smart contract-based access control system to securely manage
encrypted file sharing. Instead of re-encrypting entire files when access permissions change — an
approach that would be computationally expensive and inefficient — Tiri Vault employs an asymmetric
key-wrapping mechanism, where only the document access key is re-encrypted and stored on-chain.
This approach ensures that encrypted files stored in a decentralized storage network remain unchanged,
while access to them is dynamically managed through the blockchain.
For documents to be shared with other users a special file type/group “collaboration suite” is set. Each
file marked as a member of the Tiri Collaboration Suite is encrypted using the same ChaCha20-Poly1305
algorithm, but with a unique symmetric encryption key. Instead of encrypting files for multiple
recipients, the system encrypts only the file’s encryption key for each user who is granted access.
When a user is granted access, their public key is used to encrypt the document’s access key, and this
encrypted key is put to the Tiri Access List (TAL) smart contract. When a user retrieves the file, they
first decrypt the access key using their private key, and then use it to decrypt the file itself.
This approach allows files to remain static on decentralized storage, while permissions are managed
dynamically on-chain, preventing redundant storage and excessive gas fees.
To revoke access to a file, the file owner removes the recipient’s encrypted access key from the TAL
smart contract. Since the access key is no longer retrievable, the user loses access to the
document—even though the file itself remains unchanged in storage. This method ensures that revoked
users cannot decrypt files, even if they previously had access.
Trustless Framework
Tiri Vault extends beyond secure decentralized file storage, providing a suite of privacy-first, smart
contract-based services that eliminate centralized control over sensitive data. By leveraging smart
contracts, these services operate in a trustless, censorship-resistant manner, ensuring that users
maintain full control over their information without reliance on intermediaries. Tiri Vault implements a
zero-knowledge approach, encrypting data on the client side before committing it to the blockchain.
Tiri Vault’s trustless framework includes:
-
Passwords and text data management (Rubeus);
-
End-to-end encrypted peer-to-peer messaging (Diffy Chat);
Each of these services operates independently through dedicated smart contracts, ensuring self-sovereign
control over personal data while eliminating the risks of traditional centralized services.
Passwords & Text Storage (Rubeus)
Beyond synced file storage, Tiri Vault provides a privacy-first vault for sensitive text-based
information, including:
- Passwords
- Credit card details
- Secret and seed phrases
- Personal notes
Unlike conventional password managers, which store encrypted credentials on central servers, Tiri Vault
ensures that all stored data is encrypted client-side before being committed to the blockchain. This
guarantees zero-knowledge privacy, meaning that no entity, including Tiri Vault, has access to stored
passwords or notes.
At the core of this system lies the Rubeus smart contract, which allows users to store and retrieve
encrypted credentials using wallet authentication instead of master passwords. This approach eliminates
risks of centralized server breaches, phishing attacks, and password leaks and provides a simple but
flexible pricing model, where users can choose between paying for “put-to-contract” actions, monthly
fees or quantity subscriptions.
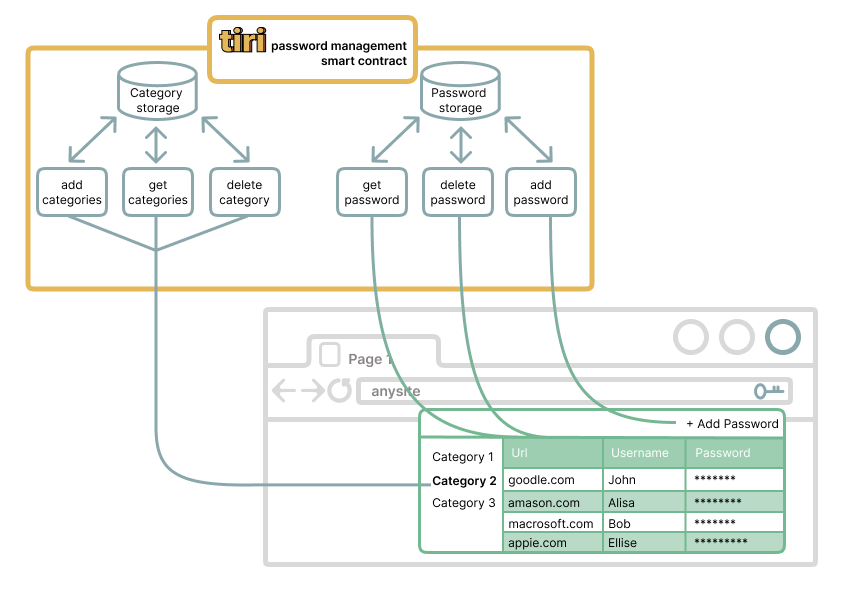
The data sent to the smart contract is encrypted using the ChaCha20-Poly1305 streaming algorithm with
message authentication. This secures transferred data from unauthorized interception and decryption as
well as malicious data substitution by a node or any intermediary. The Rubeus Smart contract enables
saved passwords, credit cards or other sensitive data to be automatically inserted into appropriate web
forms, ensuring secure and seamless authentication with unprecedented convenience and functionality, it
allows users to store any form of sensitive text, ensuring a secure, decentralized alternative to a set
of traditional applications: password managers, payment wallets, online notebooks and etc.
Decentralized Encrypted Messaging (Diffy Chat)
Collaboration in a decentralized workspace requires more than just file sharing—users also need secure
communication channels to exchange sensitive data. To address this, Tiri Collaboration Suite includes
Diffy Chat, a decentralized, end-to-end encrypted messaging system designed for secure peer-to-peer
communication. It is built upon a smart contract:
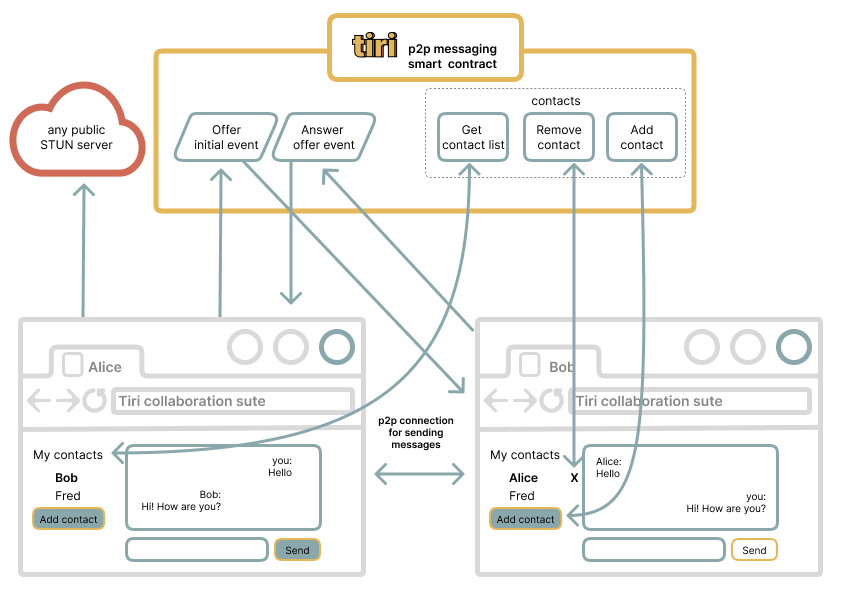
- Wallet-based authentication → Users initiate chats and verify identities using their
personal wallet credentials, eliminating reliance on usernames and passwords.
- End-to-end encryption → Messages are encrypted with a receiver’s public key, ensuring
that only the intended recipient can decrypt incoming messages.
- WebRTC-based peer-to-peer communication → Messages are exchanged directly between users
without passing through centralized servers (except the first hello-message).
- Smart contract-based session negotiation → Diffy Chat uses a smart contract to store
public keys, handle chat initiation and enable secure contact discovery.
- Public STUN servers for NAT traversal → Allowing users behind firewalls or private
networks to establish direct communication.
This approach ensures that all messages remain private, censorship-resistant, and untouchable by
intermediaries, making Diffy Chat a secure alternative to mainstream messaging platforms—suitable for
individuals, corporations, and industries requiring strict confidentiality (e.g., medical, financial,
legal sectors).